Our ransomware protection product defends ransomware beyond AI boundaries.
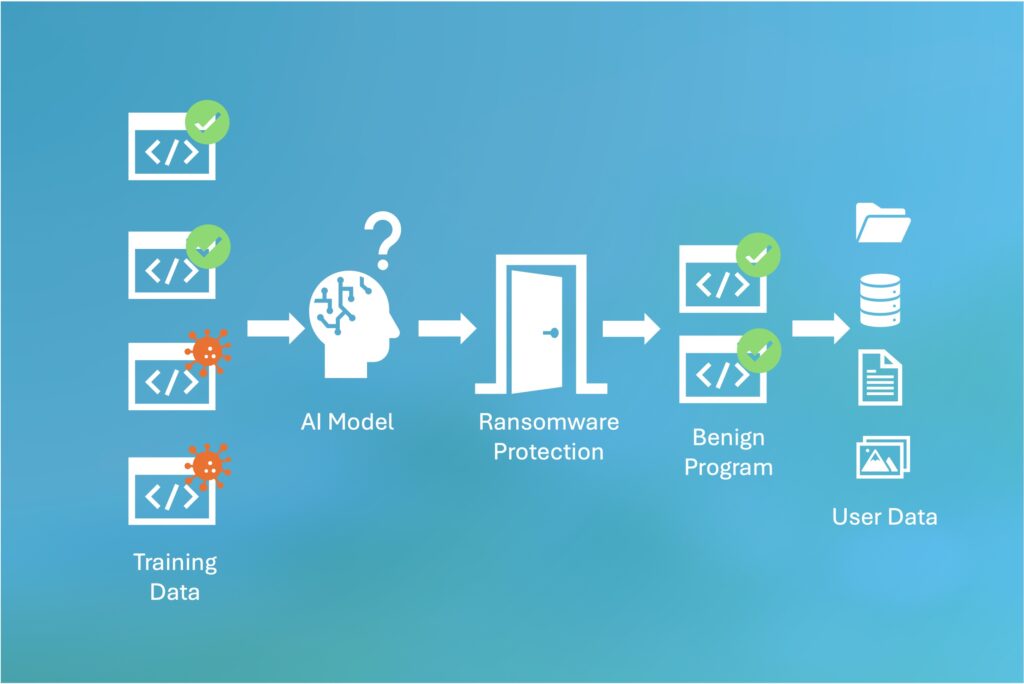
• Most existing ransomware protection software all use some AI-based technologies to detect ransomware. Basically, when a new program is about to be installed on the operating system, the ransomware protection software uses an AI model to infer whether the program is malicious or not. The major limitation is that the AI model is mainly effective in identifying ransomware similar to the ransomware that the model has been trained on.
• For a new type of ransomware that exhibits different patterns from any existing ransomware, the AI-based model lacks the ability to capture them. This is also the fundamental cause that the ransomware attacks have been more and more successful even though almost all the computers are now equipped with some kind of anti-malware software.
• It is important to emphasize that the inability of stopping the ransomware attack by contemporary anti-malware software is seldom attributed to the victim’s computer not being updated, as the majority of companies adhere to regular system update protocols.

Our ransomware protection software adopts revolutionary approach to safeguard your data.
• Unlike other AI-based anti-malware solutions that scrutinize the features and behavior of ransomware codes, our product adopts a revolutionary approach.
• Our technologies focus on safeguarding the very files targeted by ransomware. Regardless of the appearance or code of the ransomware, our system vigilantly monitors the actual I/O operations executed on the protected files. If any unauthorized encryption attempts are detected, our product swiftly blocks the attack and notifies the user. This approach empowers our product to adapt to new and evolving ransomware threats.
No extra storage needed for our ransomware protection product to recover data.
Another standout attribute of our product is it requires no additional storage space for data recovery, ensuring that users can defend against ransomware without the need for substantial hardware or infrastructure upgrades.


Our ransomware protection product is super user-friendly.
Our product is designed to be user-friendly and unobtrusive. It operates in the background, effectively safeguarding user files without interfering with the regular user experience. Users can continue editing their protected files using familiar applications without disruptions.

